Organisations generate millions of system logs every day from the likes of servers, firewalls and network devices. Their ability to process, analyse and react to this information affects how they will manage any security risks and incidents. To help process this data, many organisations implement a Security Incident and Event Management (SIEM) system or outsource to a Cyber Security Operations Centre (CSOC) for their monitoring, which provides a real-time analysis of security alerts.
No matter how sure you are that your network is secure, you may still be at risk of cyberattacks. It's no exaggeration Cybercriminals are constantly working to stay one step ahead of organisations and security professionals, exploiting any vulnerability they can in even the most sophisticated systems.
It's well-established that security is an essential part of all infrastructure. With data protection more of a concern for customers and end users than ever - particularly in light of regulations like the Cloud Act and GDPR - it's vital that organisations demonstrate a clear commitment to the security of their networks, Cloud applications and physical devices.
The move towards Hybrid Cloud infrastructures - with on-premise solutions systems connected to Public and Private Clouds to maximise the benefits of each solution - has been in progress for a number of years now. Indeed, in 2019 it was reported that 69% of organisations were already utilising some form of Hybrid Cloud solution1. Since then, the move towards a distributed workforce in response to COVID-19 has accelerated this process, with 82% of organisations reporting that they have accelerated their Cloud adoption strategies as a result of the pandemic2.
Cloud adoption has been rising year by year for some time now, with Gartner predicting this trend to accelerate beyond 2020. It has long moved on from its earliest days, where it was largely regarded as an intriguing concept but unsuitable for enterprise-level applications. Now, with a wide range of options available - including Public, Private and Hybrid solutions - it has become a highly attractive prospect for organisations at all levels, especially against the backdrop of COVID-19 and the resulting advancement of remote working. While these trends are very much the latest stage in a long process of transformation, the pandemic has undoubtedly been the catalyst behind much recent Cloud adoption, as organisations accelerate their journeys towards a distributed workforce.
So, where does that leave us in terms of the biggest question: "Is Cloud right for my organisation?"
Now more than ever, digital security is a team effort, with staff at all levels of an organisation having an active part to play in keeping critical business data safe. With the outbreak of COVID-19, and an unprecedented volume of staff working from home, robust security policies and systems are no longer enough - each and every member of staff must consider security as a fundamental part of their developing remote working routines.
But what can each of us personally do to ensure our organisations maintain their usual standards of security for the duration of this crisis, without letting such measures detract from our day-to-day work? Here are a few starting points…
Be prepared
If you're new to remote working, don't go in blind. Take the time to re-familiarise yourself with your company's security policies (particularly any new ones for home workers) and be sure to attend any training sessions that are on offer (as many organisations are rolling out remote training sessions for home workers, there are no excuses!). This will make the transition far smoother and allow you to stay focused on your work.
Secure your router
At Exponential-e, we always say that 'your Cloud is only as good as your network'. In the same way, your remote working solution is only as good as your router. As above, make sure its password is secure (especially if you've never changed its pre-set password!) and take any recommended security measures, both from your network provider and your IT team.
Check your passwords
This is a familiar refrain in the world of data security, but it always bears repeating. Familiarise yourself with current best practice regarding password creation (there are plenty of useful resources available online for this) and avoid reusing passwords. While memorising multiple passwords for each platform you use for work is certainly inconvenient, there are many excellent password manager tools available. Ask your IT team which one they would recommend, as your company may already require employees to use a specific one.
Enable updates
We all know how irritating requests to install updates on our personal devices can be, but in our current climate, it's more important than ever. More than just keeping your own devices secure, a single instance of malware could bring down your entire company network, so don't take any chances. Ensure you install all recommended updates, or – better yet – enable automatic updates. This will ensure your devices are always protected against the latest security threats.
Ask!
As we've already mentioned several times in this post, if you are unsure about anything when it comes to data security, don't guess… ask the right person! In particular, your IT team will be more than happy to advise you about security best practice when home working, or alternatively, consider Exponential-e's Cyber Security Advisory service, which was created to provide a 'one stop shop' for any security-related concerns you may have.
In the meantime, download our Working from Home Checklist, which breaks down all the key elements of secure remote working.
Cyber professionals say that companies involved in the manufacturing industry are more exposed to cyber-attacks. This was revealed by a number of studies produced by the Manufacturers Alliance for Productivity and Innovation (MAPI). According to MAPI; 40% of manufacturing firms experienced a cyber-attack within the last year. Of those attacked, 38% of them suffered over $1 million in damages.
Ransomware is malware that encrypts an individual's files so that they no longer have access to them, and subsequently demand payment for the files to be released. Usually the payment is asked to be made in an untraceable cryptocurrency form, such as Bitcoin. The most common way ransomware ends up on an individual's computers is through email spam, which individuals will click on and open.
Unfortunately, the files cannot be decrypted without a mathematical key which is only known by the cyber attacker, and the reason why many individuals tend to pay up. However, many find that despite paying the ransom, their files remain encrypted.
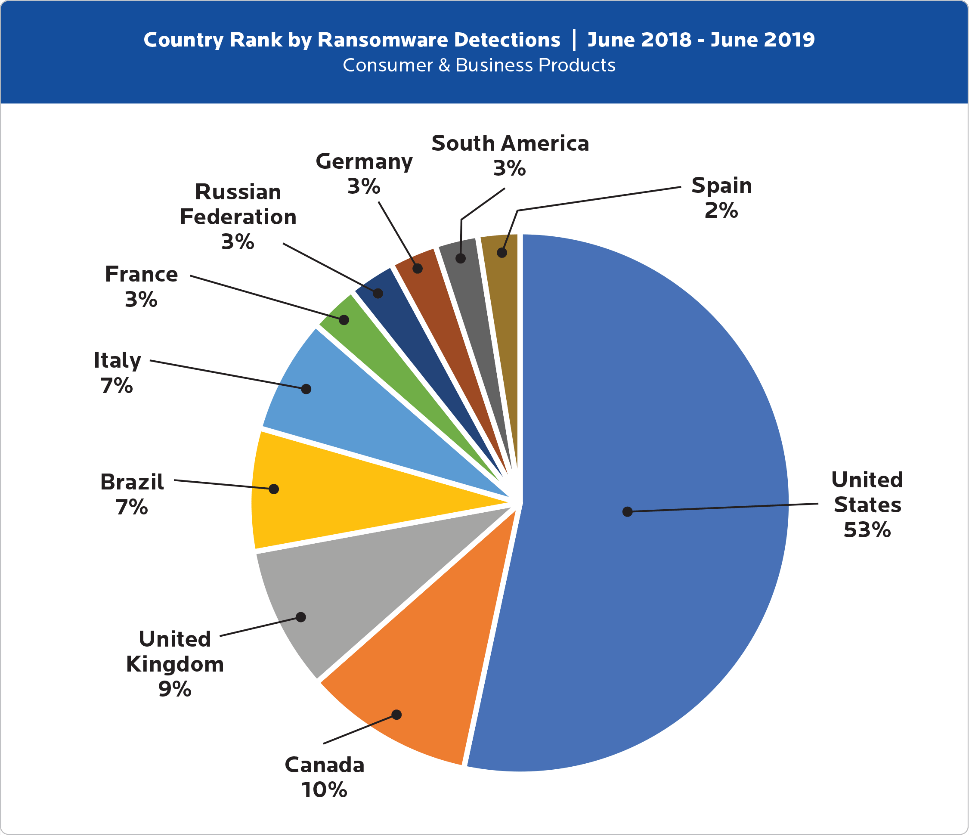
When looking at which countries were affected by ransomware attacks the most, the UK was found to have the highest percentage out of Europe:
Figure 1: Cybercrime Tactics and Techniques: Ransomware Retrospective Report, Malwarebytes
Despite the NHS facing one of the worst ransomware attacks in May 2017 - the WannaCry ransomware attack - which cost the NHS £92m and caused more than 19,000 appointments to be cancelled (The Department of Health), this chart clearly highlights how organisations in the UK still need to invest more into their Cyber Security solutions to stay protected from ransomware attacks.
At Exponential-e, we help organisations that have been affected by ransomware attacks. Our Head of Cyber Consultancy, Mark Belgrove, discusses a real-life cyber attack in the video below, and shares how Exponential-ehelped mediate the situation.
Phishing is the fraudulent use of electronic communications to try and obtain sensitive information, such as usernames, passwords and credit card details by posing as a legitimate institution. Phishing attacks attempt to get individuals to click on a malicious link and enter confidential information to steal their identity, funds or to be the first step in a serious cyberattack against an organisation.
All organisations store data, and regardless of whether it's a recipe or an algorithm, this data is an organisation's most prized asset, which is why hackers make it their target. The Cyber Security Breaches Survey 2019 from the Department for Digital, Culture, Media & Sport (DCMS) found that 32% of businesses identified cyber security breaches or attacks in the last 12 months, which have cost an average of £4,180 in lost data and assets
Cybercriminals are only getting more cunning and skilful with their cyber attacks, which is bad news for organisations when it comes to meeting privacy and compliance regulations. There can be significant legal implications for organisations if their data is not secure and regulations are not met. For instance, since the GDPR (General Data Protection Regulation) came into effect in May 2018, data protection regulators have imposed 114 million euros (approximately 97 million pound) worth of fines under the GDPR regime (GDPR Data Breach Survey 2020 by DLA Piper).
The turbulence of the current geopolitical situation has affected numerous sectors, who must not only consider how to protect their infrastructure from anticipated cyber-attacks, but also ensure that they are able to maintain business-as-usual as possible against a backdrop of global disruption to supply chains. As a sector that depends on the ready availability of materials, the UK's AEC sector has been particularly affected.
Although the sector as a whole has traditionally been comparatively wary of the ever-increasing pace of technology, legal services are increasingly data driven, with an abundance of AI-related discussion emerging within legal technology circles. The core Document Management Systems (DMS) and Practice Management Systems (PMS) remain the centre of focus for how and where to deploy a variety of rapidly maturing SaaS platforms, or dedicated, highly customised suites.
Retailers - be they small local shops, online sellers, or top global brands - generate, transfer, and store more data than ever before, ranging from customer data (both online and in-store, as we have considered in previous articles), to supply chain and asset tracking data. Whether it's shopping online or utilising in-store apps to access the latest savings and special offers, the way customers shop has fundamentally changed forever, with the data they generate online and in person allowing retailers to build up unique personas that drive truly bespoke experiences.
With fundamental shifts in consumer behaviour, changing economic conditions, and a rapidly evolving regulatory environment, it's a challenging but exciting time for the UK's retail sector, and technology has a key role to play. In particular, advances in IT and networking solutions are empowering retailers to enhance their operational efficiency, improve the customer experience, and retain their competitive edge in an increasingly online and interconnected world.
The nature of AEC projects and the high volumes of sensitive data firms generate, transfer, and store on a daily basis make them a natural target for cyber criminals. Indeed, a recent Government study found that 5% of building firms have already fallen victim to some form of cyber-crime in the just a year, but that 26% of them still did not have adequate cyber security measures in place.
In October 2023, the British Library suffered "one of the worst cyber incidents in British history," as described by Ciaran Martin, ex-CEO of the National Cyber Security Centre (NCSC).
The notorious Rhysida ransomware gang broke into one of the world's greatest research libraries, encrypting or destroying much of its data, and exfiltrating 600 GB of files, including personal information of British Library staff and users.